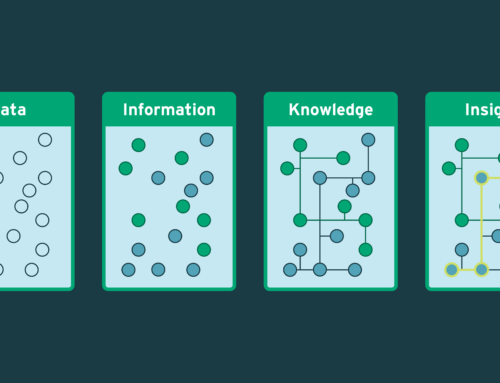
Not If, but When
It’s no longer if you will become a victim of computer crime, but when. Knowing we live in this type of hostile environment is critical to understanding where to start when building a security posture. The heart of a modern company is its data. Protecting this data is no longer the responsibility of just the Information Security team – all users need to participate for protection to be successful. By using multiple layers of security tools and best practices, you can ensure you are doing all you can to assist in keeping data secure.
The Matching Game
Start by finding the organization that outlines regulations or compliance for your industry:
- If you’re in healthcare dealing with patients’ records, you will need to follow HIPAA & HL7 standards.
- If you’re processing credit cards with an in-house credit card processor, you will need to be in compliance with PCI DSS standards.
- If you’re a DoD vendor, then the CMMC is critical for gaining future work within the Defense Industrial Base.
- You can always fall back on the NIST guidelines, which could also be the basis of other regulations.
- There are other international standards that could be applicable to you, like ISO 27001.
- Be sure to sign up to receive security alerts from CISA.

By identifying your governing body, you can identify the minimum standards that your organization needs to attain. These are considered minimum standards because security is a layered approach. It isn’t just a firewall, antivirus, multi-factor authentication, and password changes that are needed. While important, they’re only the beginning of a strong security posture and plan.
One of the most important aspects of your company’s security posture must be end-user training. “Must” may seem like a strong word here, but “88% Of Data Breaches Are Caused By Human Error.” Using an active end-user training program that covers proper password/passphrase use, how to spot Phishing attempts, the importance of locking workstations, and physical security concepts is a must. If your system isn’t proving these topics (and more), then you should investigate other options. The KnowBe4 offering has provided training on these topics and produced positive results at Mile 2.
Partners and Tools
A platform like KnowBe4 is one of many tools in the security toolbox. Based on the standards within your industry, you should look for tools that have a successful and proven track record. For example, while just having Microsoft 365 GCC High doesn’t make you CMMC compliant, it does offer specific settings that will allow your company to achieve a CMMC score that might not be possible using the commercial Microsoft 365 offering.
Having a cloud vendor that is knowledgeable in your industry is critical for achieving and maintaining industry compliance. These proven vendors should be seen as long-term partners who want to help you succeed. Your partners should be able to assist with very specific details of your security plan – details around not only device and account management, but also helping to test that these settings are in use and being practiced. The tools (or team depending on budget) should be looking at the log files to ensure that proper role-based access controls (RBAC) are set up and in use. There might be model audit rule (MAR) processes to ensure certain group access or ownership is reviewed. These are critical reviews, especially as solutions become more interconnected.
Resiliency and Hand-offs
Speaking of interconnected solutions, be sure that your long-term solutions include investigating, monitoring, and improving the resiliency of the systems. Don’t simply rely on the bells and whistles to alert you when there are problems. Be proactive and work towards the “chaos monkey” level of resiliency. Start with this end in mind so that there is less rework as you iterate, grow, and mature your solutions. Knowing the hand-offs between systems and the importance of joint system performance will be critical when there is an issue and the finger-pointing or blame game starts. Ensure you, your team, and your partners participate in the business continuity test and disaster recovery scenarios.
With nearly 30% of hacks happening from insecure websites, it is imperative to put security in the DevSecOps process. If you are developing your own code, be sure that your pipeline has static & dynamic application security testing (SAST & DAST) happening so that you can identify vulnerabilities as early as possible. Many teams are taking it further and introducing interactive application security testing (IAST) and runtime application self-protection (RASP) to do advanced testing of their web-based application.
Small Steps and Insurance
There are all sorts of crazy things happening on the internet and the dark web. For instance, Caffeine is a new Phishing as a Service for hackers where they can have spear phishing attempts targeting you and your staff in minutes. Ensure that you are changing passwords, using passphrases, not sharing passwords or accounts, and monitoring the use of systems for suspicious connections from overseas. Start small and create the plan and roadmap to get where you want to go. Create the quarterly backlog and prioritize the tasks based on resources and funding.


A well-funded Cyber Security budget should be seen as an additional insurance policy. You hope you never need insurance, but you do have it. You keep it up to date to ensure you are doing all you can to reduce the threat to you and your data. An umbrella or cyber insurance policy is also a must-have these days. Stay alert for suspicious activities, emails, and text messages. Be safe, it’s a crazy world out there. Should you need assistance with designing and building resiliency into a new or existing application, please connect with us!